Top Cyber Threats: A Quick Reference Guide

The cyber threat landscape continues to evolve, and organizations face a variety of attacks. This guide serves as a quick reference to the most common cyber threats today. It breaks down how to detect, investigate, and respond to these threats, helping security teams act fast and effectively. If you're looking for an easy way to stay prepared, this cheat sheet provides practical, actionable insights.
1. Phishing Attacks
Phishing remains one of the most common methods used by attackers, relying on social engineering to steal credentials or trick users into downloading malicious software.
Detection: Suspicious emails, unusual login activities.
Areas to Investigate: SIEM, Email Filtering Logs, User Reports, DNS Logs, Web Traffic.
Prevention & Response: Use advanced email filters, conduct phishing simulations, and regularly train employees to recognize phishing attempts.
2. Ransomware
Ransomware attacks are notorious for encrypting data and demanding payment for the decryption key, leading to potential data loss and severe business disruptions.
Detection: Sudden file modifications, ransom notes, EDR/Antivirus alerts, unusual network activities such as Command-and-Control (C2) connections and data exfiltration.
Areas to Investigate: SIEM, EDR/XDR Platform, Antivirus Logs, System Logs, Network Traffic, DLP Solution Logs.
Prevention & Response: Isolate infected systems, run antivirus scans, notify law enforcement, and use resources like NoMoreRansom.org to attempt decryption without paying the ransom.
3. Vulnerabilities
Attackers exploit unpatched vulnerabilities in software and hardware to gain unauthorized access, often using these weaknesses for privilege escalation or persistence within a network.
Detection: Unexpected system behavior (privilege escalation, persistence), Anti-Exploit reports.
Areas to Investigate: Vulnerability Scans, Patch Management Logs, System Audits, Anti-Exploit Logs.
Prevention & Response: Regularly update and patch all systems, conduct vulnerability assessments, and assume that zero-day vulnerabilities exist within your network.
4. Business Email Compromise (BEC)
BEC attacks involve unauthorized access to a business email account, which is often used to trick employees or clients into transferring funds or revealing sensitive data.
Detection: Unusual email activity, unauthorized financial transactions, phishing reports.
Areas to Investigate: User’s System Logs, Email Logs, Network Traffic, User Reports.
Prevention & Response: Quarantine affected accounts, reset passwords, educate employees on phishing tactics, and implement multi-factor authentication (MFA).
5. Cloud Security Breaches
As cloud services become a critical part of business operations, misconfigurations and security gaps in cloud platforms can expose sensitive data to unauthorized access.
Detection: Unauthorized access attempts, data leaks, unusual cloud resource usage.
Areas to Investigate: Cloud Service Logs, Access Logs, Network Traffic.
Prevention & Response: Implement CASBs (Cloud Access Security Brokers), enforce multi-factor authentication, encrypt data, and conduct regular cloud security audits.
6. Social Engineering Attacks
Social engineering exploits human psychology rather than technical vulnerabilities. Attackers manipulate individuals into revealing sensitive information or performing actions that compromise security.
Detection: Reports of suspicious interactions, unusual account activities.
Areas to Investigate: User Reports, Communication Logs, Access Logs.
Prevention & Response: Train employees to recognize social engineering attempts, enforce strong access controls, and use MFA to prevent unauthorized actions.
7. Insider Threats
Insiders, whether employees or contractors, can misuse their legitimate access to sensitive systems to steal data, sabotage systems, or otherwise harm the organization.
Detection: Unusual data access patterns, unauthorized data transfers, suspicious behavior.
Areas to Investigate: Employee Activity Logs, Access Controls, Network Monitoring.
Prevention & Response: Monitor user activities closely, enforce least privilege access, and provide security training focused on insider threats.
8. Denial of Service (DoS/DDoS)
These attacks involve overwhelming a system or service with traffic, rendering it inaccessible to legitimate users. DDoS attacks are often employed for extortion or to disrupt operations.
Detection: Extremely high network traffic targeting a server or service, possible ransom demands.
Areas to Investigate: Traffic Monitoring, Anti-DDoS Solution Logs, Firewall Logs, System Logs.
Prevention & Response: Patch vulnerabilities, work with your ISP, filter traffic, and apply rate limits using a CDN or edge-network firewall.
9. Supply Chain Attacks
Attackers target an organization's vendors or partners to gain access to critical systems, making supply chain attacks complex and often difficult to detect.
Detection: Unusual network traffic, unusual endpoint behaviors, alerts from supply chain partners.
Areas to Investigate: Vendor Communications, Network Logs, Systems Access Logs, Systems Activities Logs.
Prevention & Response: Monitor third-party access closely, enforce security policies for supply chain partners, and conduct regular security audits.
10. IoT and Industrial IoT Attacks
IoT devices, often with minimal security, are increasingly targeted by attackers looking to access sensitive data or disrupt critical infrastructure.
Detection: Unusual device behavior, network anomalies.
Areas to Investigate: IoT Device Logs, Network Traffic, Firmware Updates.
Prevention & Response: Implement strong authentication, regularly update device firmware, segment IoT devices, and ensure that admin interfaces are not publicly exposed.
11. Advanced Persistent Threats (APTs)
APTs involve long-term, targeted cyberattacks, often initiated by nation-state actors or highly sophisticated criminal groups. The goal is to maintain access to a network undetected for extended periods.
Detection: Persistent network anomalies, data exfiltration, unauthorized account creations.
Areas to Investigate: Network Logs, Access Logs, System Processes, Incident Response Teams.
Prevention & Response: Continuously improve your security posture, isolate affected systems, initiate a forensic investigation, and escalate incident response efforts.
Bonus Resource
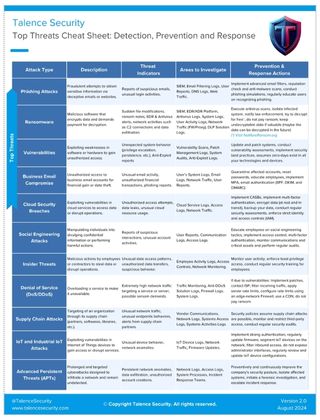
Top Threats Cheat Sheet
For quick access to all the information outlined above, check out our detailed Top Threats Cheat Sheet: Detection, Prevention, and Response. It’s a valuable reference tool that can help your team better manage and respond to today’s most prevalent cyber threats.
Download it here




