Adversary Profiles: Understanding Cybersecurity Threat Actors
Understanding your cybersecurity adversaries is crucial for building effective defenses. From nation-state actors pursuing geopolitical agendas to cybercriminals focused on financial gain, each adversary has unique motivations and uses specific tactics to achieve their goals. Knowing these factors helps organizations anticipate potential attacks and tailor their defenses accordingly. In this post, we explore the key adversary profiles that every security team should be aware of, breaking down their strategies, methods, and the impact they can have. This knowledge is essential for crafting more targeted defense and response strategies.
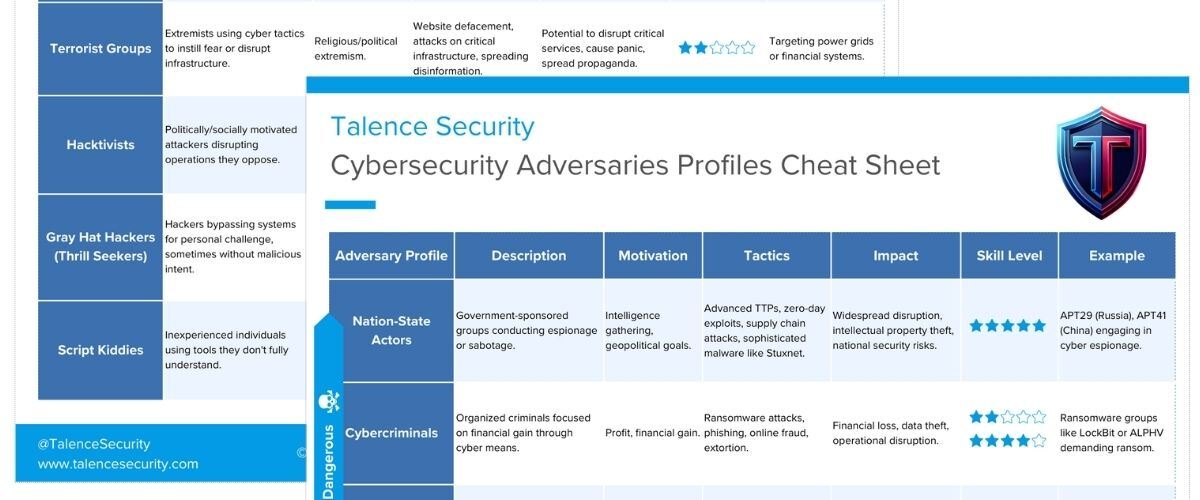
1. Nation-State Actors
Nation-state actors are typically government-sponsored groups conducting cyberattacks with a geopolitical agenda. These actors often use advanced persistent threats (APTs) to gather intelligence or cause disruption.
Motivation: Intelligence gathering, geopolitical goals.
Tactics: Advanced TTPs (Tactics, Techniques, and Procedures), zero-day exploits, supply chain attacks, sophisticated malware (e.g., Stuxnet).
Impact: Widespread disruption, intellectual property theft, national security risks.
Example: APT29 (Russia), APT41 (China) engaging in cyber espionage.
2. Cybercriminals
Cybercriminals are organized groups or individuals focused on financial gain through various cyber tactics. They often leverage ransomware, phishing, and online fraud to target businesses and individuals.
Motivation: Profit, financial gain.
Tactics: Ransomware attacks, phishing, online fraud, extortion.
Impact: Financial loss, data theft, operational disruption.
Example: Ransomware groups like LockBit or ALPHV demanding ransom from businesses.
3. Insiders
Insiders are employees or contractors with authorized access to sensitive information, who misuse their access for financial gain or revenge. These attacks can be hard to detect due to the insider’s privileged access.
Motivation: Financial gain, revenge, coercion.
Tactics: Data theft, sabotage, espionage, leaking confidential information.
Impact: Often severe due to access to sensitive information.
Example: Edward Snowden leaking classified NSA information.
4. Corporate Espionage
Corporate espionage involves businesses spying on competitors to gain an advantage. These attackers typically use phishing, insider threats, or bribery to steal trade secrets or intellectual property.
Motivation: Corporate gain.
Tactics: Phishing, insider threats, bribery, cyber infiltration.
Impact: Loss of competitive advantage, financial loss, IP theft.
Example: Hiring hackers to steal trade secrets from competitors.
5. Cyber Mercenaries
Cyber mercenaries are hackers or groups offering their services to the highest bidder. These attackers can be involved in anything from launching DDoS attacks to ransomware deployment and industrial espionage.
Motivation: Profit-driven.
Tactics: DDoS attacks, ransomware deployment, industrial espionage.
Impact: Ranges from minor disruptions to significant economic losses.
Example: DDoS-for-hire services or malware development sold on dark web markets.
6. Terrorist Groups
Terrorist groups use cyber tactics to spread fear, disrupt critical infrastructure, or propagate disinformation. These groups may target power grids, financial systems, or other high-value targets.
Motivation: Religious/political extremism.
Tactics: Website defacement, attacks on critical infrastructure, spreading disinformation.
Impact: Potential to disrupt critical services, cause panic, spread propaganda.
Example: Targeting power grids or financial systems.
7. Hacktivists
Hacktivists are politically or socially motivated attackers aiming to promote their cause by disrupting the operations of organizations they oppose.
Motivation: Ideological, political, social causes.
Tactics: Website defacement, DDoS attacks, data leaks, doxing.
Impact: Minor disruptions to significant reputational damage.
Example: Anonymous targeting organizations they perceive as unethical.
8. Gray Hat Hackers (Thrill Seekers)
Gray hat hackers, or thrill seekers, often hack into systems for personal challenge or curiosity, sometimes without malicious intent. However, their actions can result in accidental damage or exploitation by more malicious actors.
Motivation: Curiosity, personal challenge, ego boost.
Tactics: Penetration testing-like activities, exploiting vulnerabilities for fun.
Impact: Accidental damage or exploitation by malicious actors.
Example: A hacker exploiting vulnerabilities for personal satisfaction or prestige.
9. Script Kiddies
Script kiddies are inexperienced individuals who use existing tools or scripts they don’t fully understand. Despite their lack of skill, they can still cause harm, particularly to unpatched systems.
Motivation: Seeking recognition, entertainment, proving a point.
Tactics: Use of automated tools to exploit known vulnerabilities.
Impact: Typically low-level damage, but unpatched systems remain vulnerable.
Example: Teenager using a botnet service for a DDoS attack.
Bonus Resource
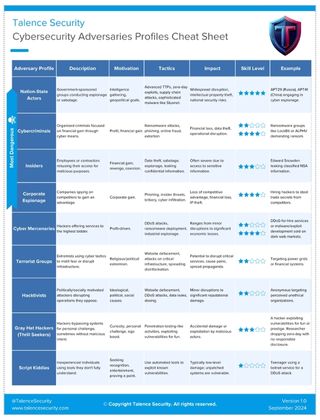
Adversary Profiles Cheat Sheet
For quick access to all the information outlined above, check out our detailed Adversary Profiles Cheat Sheet. It’s a valuable reference tool that can help your team understand and mitigate threats from different adversaries in the digital landscape.
Download it here




